Hi,
Welcome to my article about Python Scripting for Administration and Automation Management Network Device used Paramiko Part 2, in previous section i was introduce to you about what is python paramiko, and what we can do used paramiko in our infrastructure operation.
oke i help you to remember, Paramiko is python interface around SSH networking, this method was used on Ansible as Configuration management, remote execution, automation deployment, to your system and IT infrastructure without agent installation on your system (Agentless). so in this article i used paramiko with a little bit python scripting to create simply tools application and used that tools to remote my network device or system to get information what i need used remote execute command. to do configuration task, i will show you on next section.
i was show to you from previous section (Paramiko-Part1) how to install and used python-paramiko to execute script and create remote session to remote device, so i assumed you have understand and i can continue to python script and explanation.
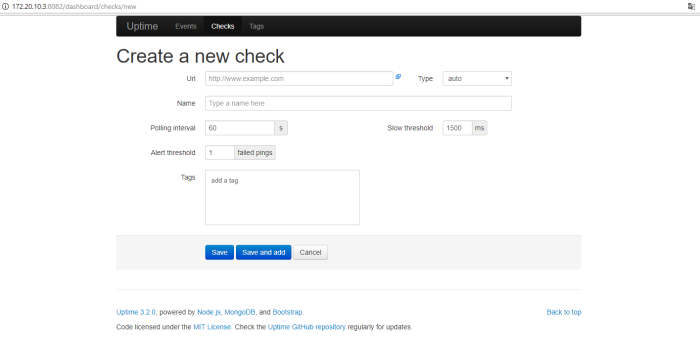
create python script on your linux system (i used Ubuntu 14.04 LTS) with command
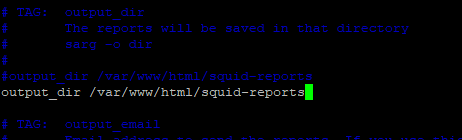
#vim paramiko-show.py
i will separate script and give the explanation
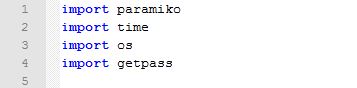
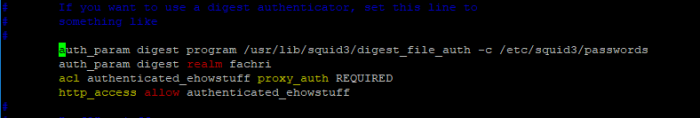
#Noted : on this part i declare and import module paramiko to python script so i can called that module when i execute my script
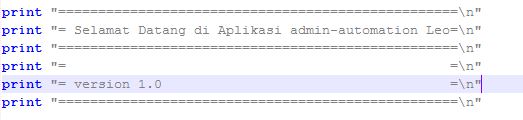
#Noted : This is Banner my application tools (its funny right..LuL)
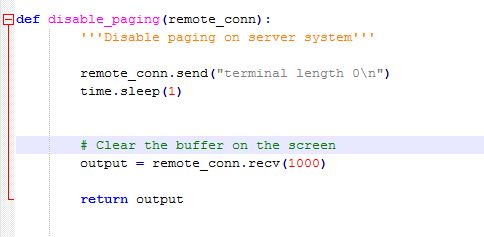
# Noted : this pieces is code initialization i create remote connection from my terminal, do sleep session in one second “time.sleep(1)” till remote session created done and save output remote session to variable named “output”
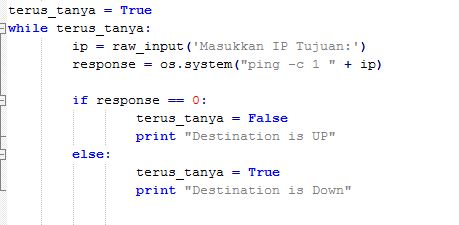
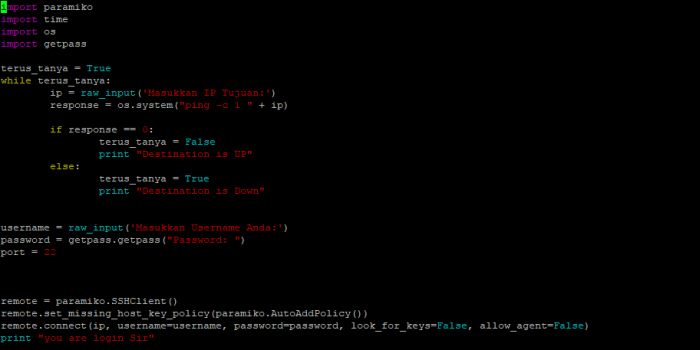
#Noted : This Script is python while loop to check are host destination we want to remote is on UP or Down Condition, user will input Address destination host which will remote and save the value on variable “ip”, and do command “ping -c 1” to ip destination (ping at once count) used “module os” i have import at top and save the value to variable response. next i do python if and else condition in python while loop function, if the value variable “response” while loop is Zero (Success) print command in terminal “Destination is UP” while loop will be end “False” and execution will continue to next script, if the value “response” other than Zero, print command “Destination is Down” and looping will be happend and ask user to input destination host
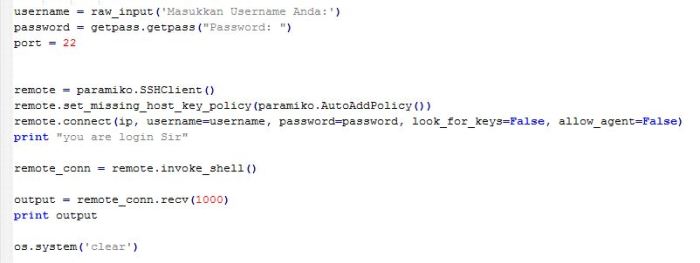
#Noted : on this piece code i used raw_input string to get value from user, and save the input to variable username for username user, and password to password input from user, i used getpass portable password input to hide value password user when they write it on terminal.
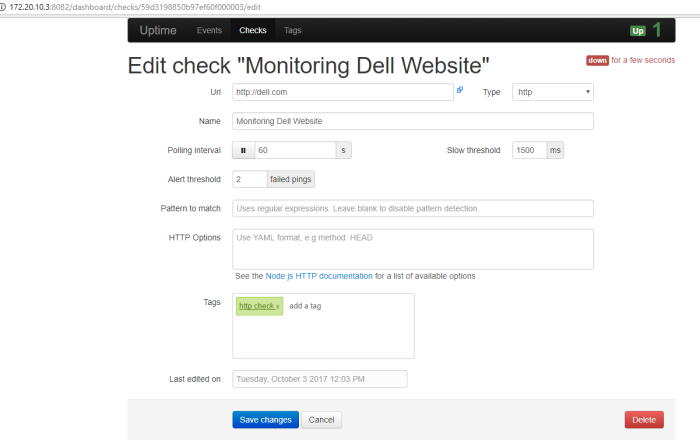
on the second piece script i do python paramiko function to called SSH client and do remote connection used value on variable “ip, username, and password”, then when connection success terminal will print info “you are login sir”, show result remote session and clear terminal when its done
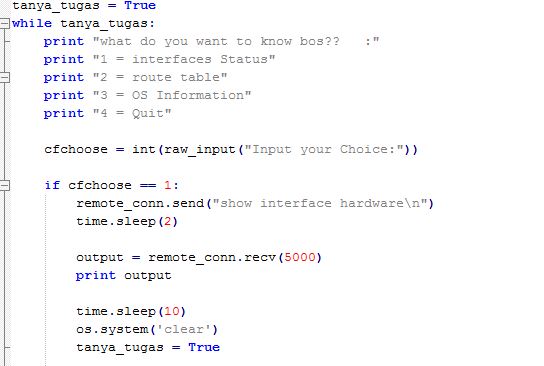
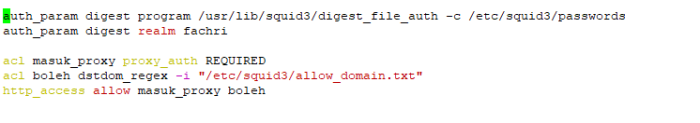
Note : in this piece code i do python while loop again to choose menu section after we success login to system the remote host, this menu is option to get information or status from your remote host/device, on this example i created remote command to get information from my palo alto firewall like Interface status, route table and software information through choose option.
user will give they inpute choose on integer value and we will save that value on variable “cfchoose“, then from that input user value on variable cfchoose we will create if else condition on python while loop choose menu section.
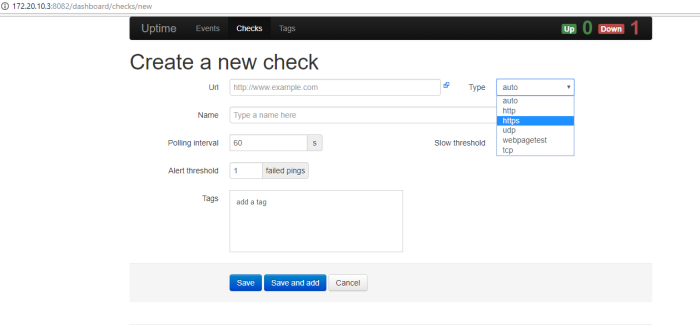
if user give the integer input number 1 which that mean want to know interface status palo alto device, paramiko will send remote command palo alto “show interface hardware” to get information interface status of palo alto device, do time sleep on 2 second till all the output success shown, then save that result on variable “output” and print it to our terminal. do time sleep on 10 second till user done to see and capture the result then do clear terminal and looping back to choose menu option
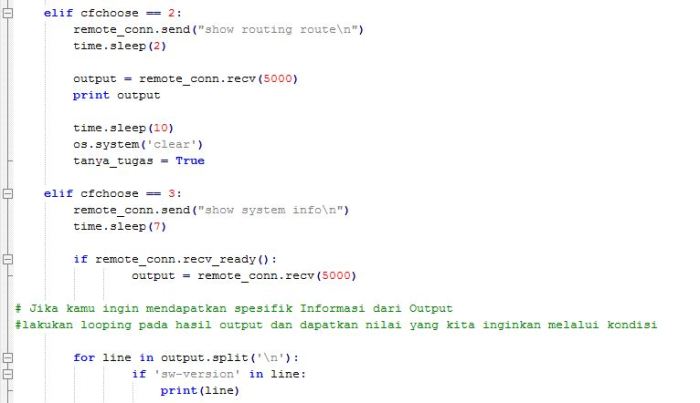
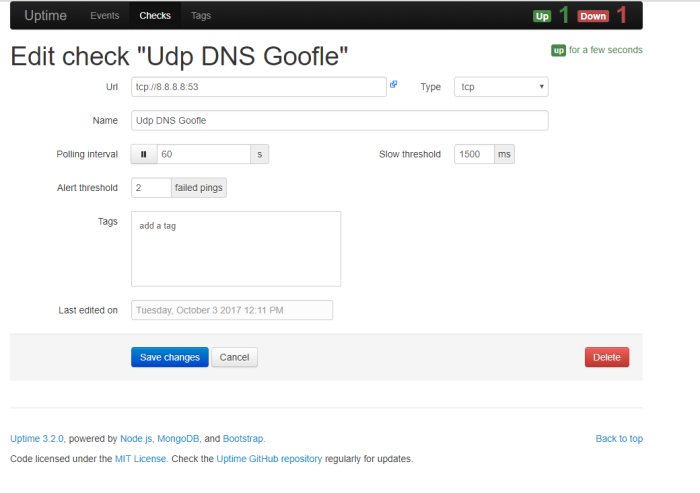
Note : in the example script above, if user choose option number 2 which mean user want to show routing table in this terminal from remote palo alto device, paramiko will send remote command palo alto to show the route table that firewall device with comamnd “show routing route”, do sleep time till all output from remote command shown and save the value to variable output, then show that result to the terminal. next do time sleep on 10 second so user can see and capture the result, before we clear terminal output and looping back to choose menu options
Next section if user choose option number 3 which mean want to know OS version of palo alto firewall device, paramiko will send remote command to palo alto via SSH to get system information used command “show ystem info”, this command will show to you about all system information of palo alto device, like hostname, SN, OS version, Wildfire and many more, but in this case we just want get specific information from that all value we can get from system information, i just want to know the OS version so in this case i used another method from 2 script cfchoose section we have seen before, after do remote command to palo alto, i save the value to variable output, then i do for loop python on section if else cfchoose, i will loop all value i have save on variable output and put it on variable line and do if condition againts, if on this loop i get ‘sw-version’ i will put that value on variable line and show it to the terminal, next do time sleep on 10 second so user can see and capture the result, before we clear terminal output and looping back to choose menu options
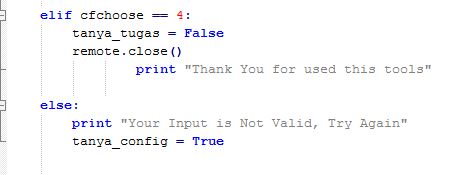
Note : if user choose option number 4 which mean user want to exit from this application, script will stop python while loop for choose menu option, close remote session SSH to remote host/device and print information “thank you for used this tools”
and the last is “else” the negative condition, it will show when input user on while loop choose menu option is not valid, it will print info “Your input is not valid, try again” then do looping back to input user on choose menu option
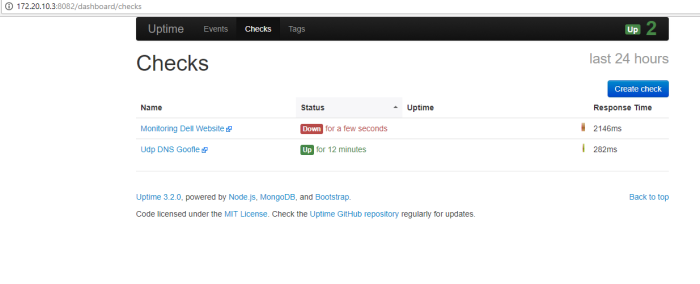
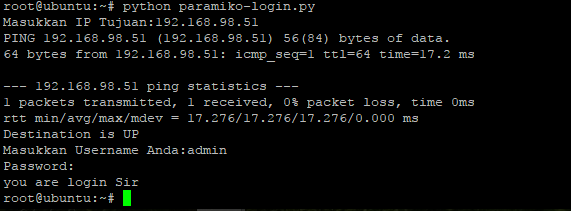
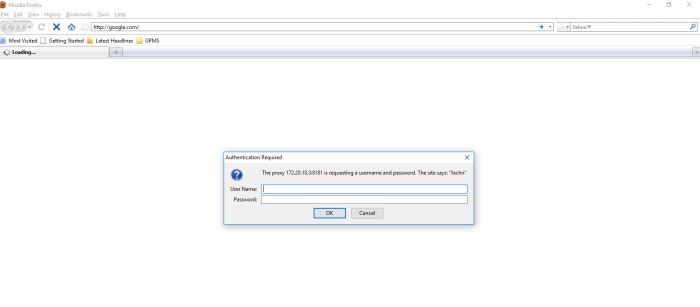
In the picture below i show to you how this application is working :
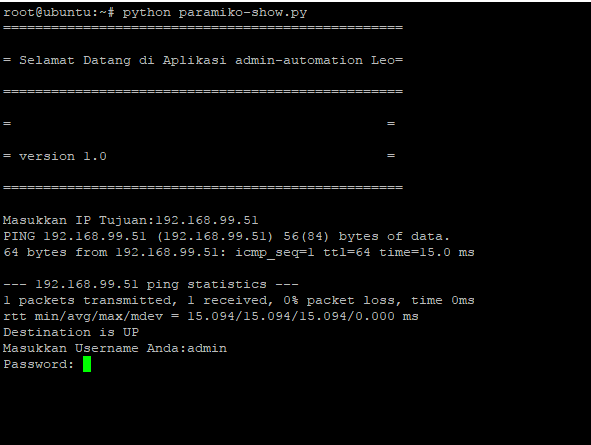
picture above is section when i run the python script, input address remote host/device and login used my cridential to palo alto device
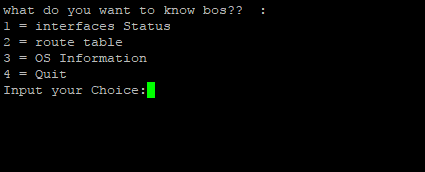
after we success login, we will see choose option menu, to choose what we will do from their option menu
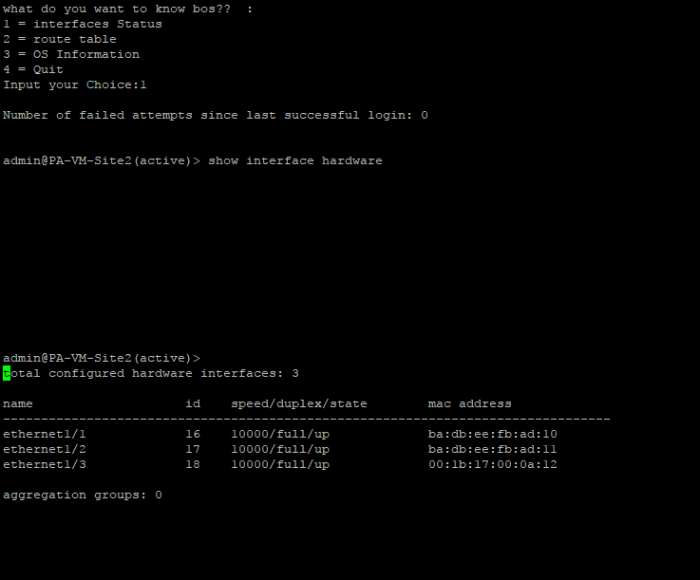
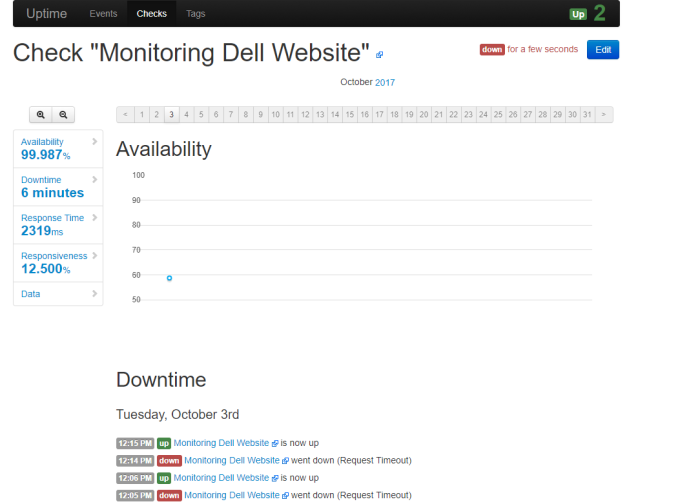
picture above is example if we choose option one which mean, want to know interface status of palo alto firewall
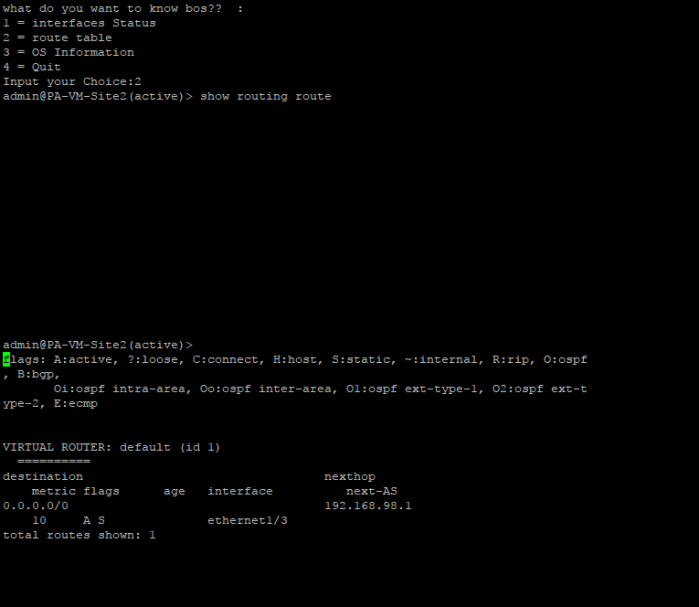
picture above is example if we choose option 2 which mean show route table of palo alto device
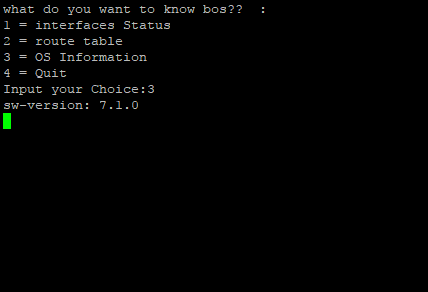
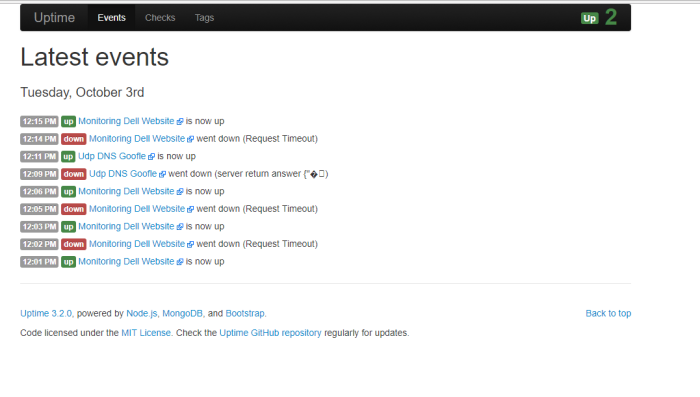
picture above is example if we choose option 3 which mean show OS Version palo alto device from system information value
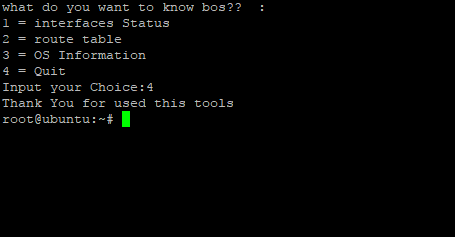
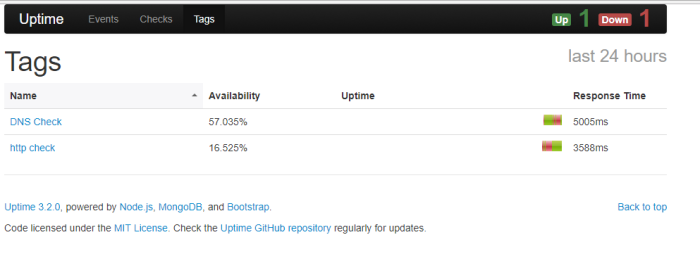
picture above is example if we choose option 4 which mean want to out from this application
Full Script
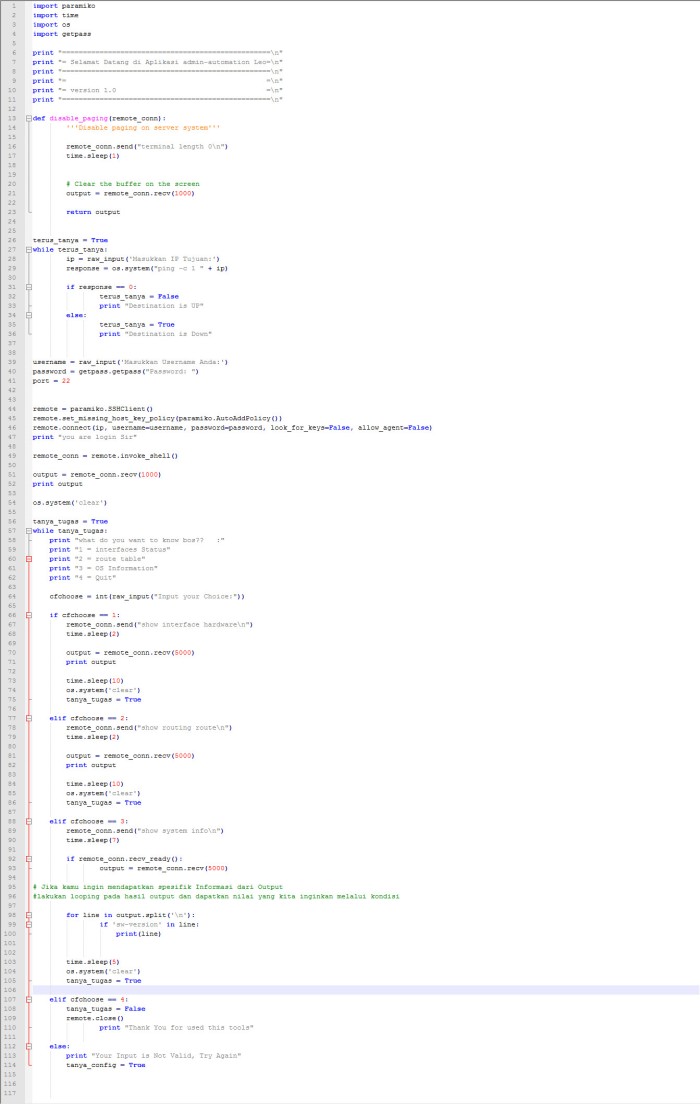
Okay , thats all i can share to you on this article, on the next section we will try to create application configuration for network device used python paramiko scripting
Thanks

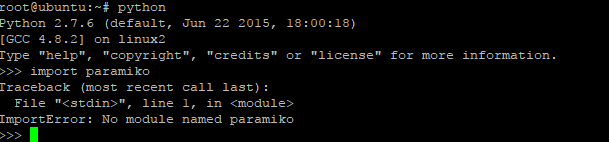



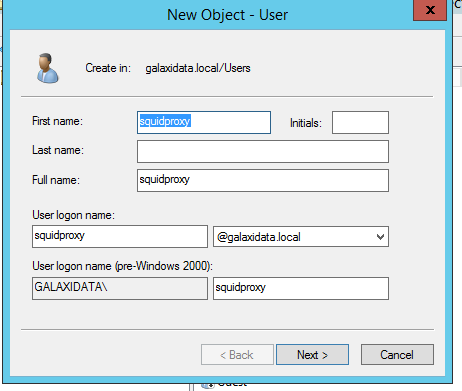
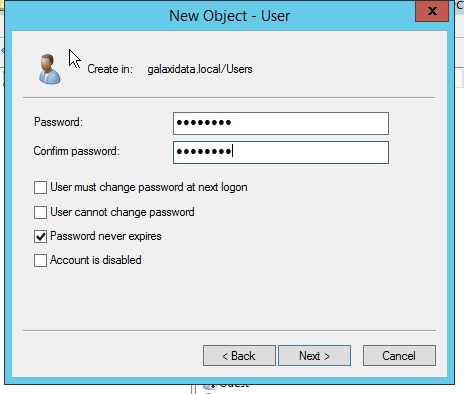
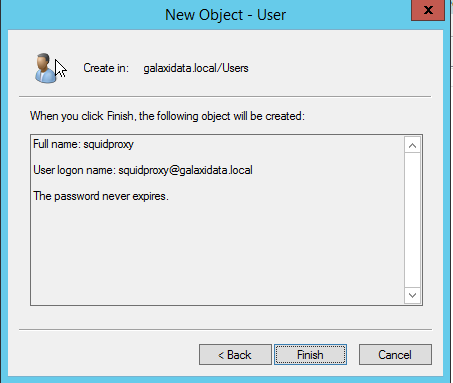
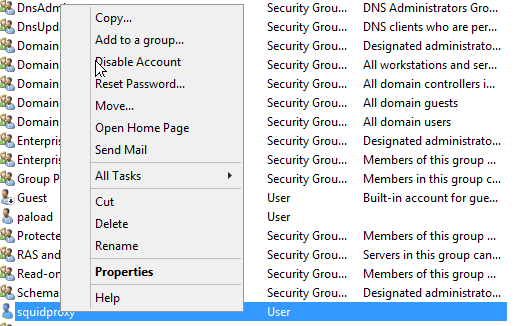
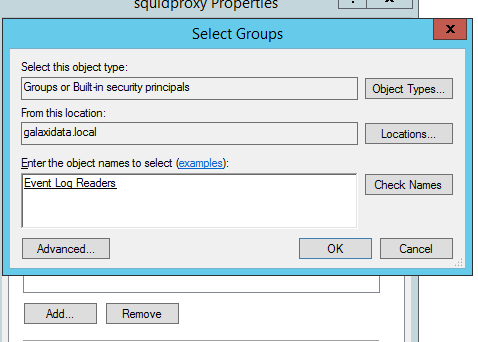
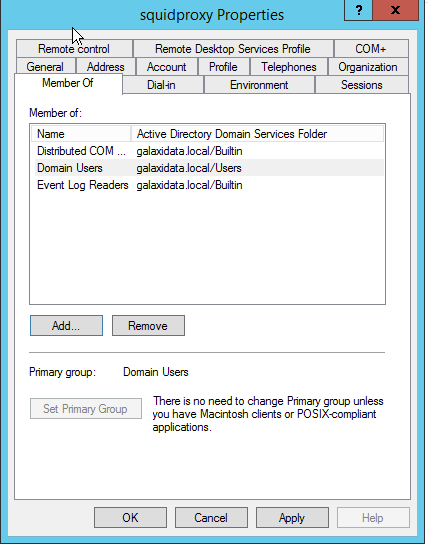
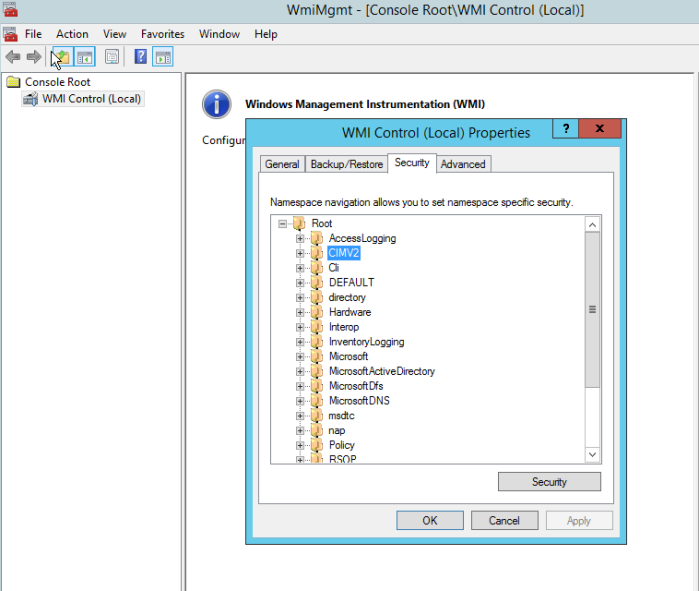
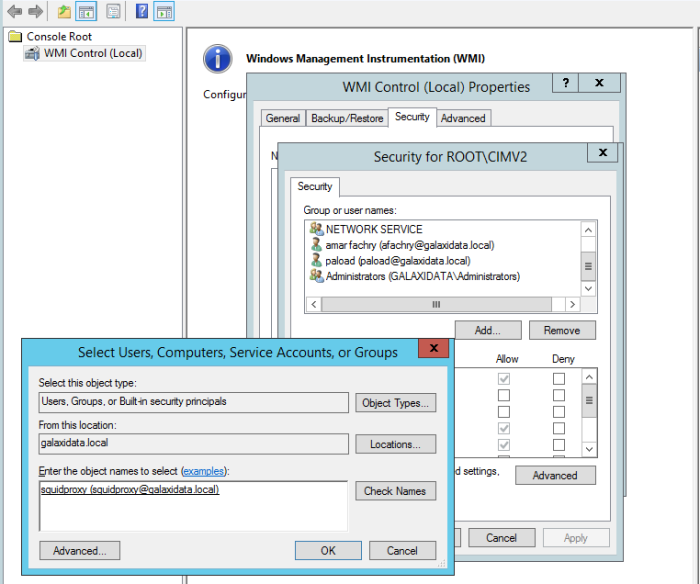

 Thats all i can share to you on this article, good luck
Thats all i can share to you on this article, good luck